SQL INJECTION INTRODUCTION--
- SQL Injection is the most common vulnerability on the internet.
- It is mainly flaw in the web application & not a Database or web server issue.
- most programmer are still not aware of this threat.
- Sql injection is a technique used to take advantage of non-validate Input vulnerabilities to pass SQL commands through a web Application for execution by back-end Database.
- In Other words,Sql injection is a basic techniques /attack used to either gain unauthorised access to a database or to retrieve information directly from the Database.
- Authentication Bypass --- Using this attacks, an attacker logs on to an application without providing valid username & password & gain the administrative privileges.
- Information Disclosure --- Using this attacks, an attacker obtain the sensitive Information that is stored in the database.
- Compromised Data Integrity --- An attacker uses this attack to deface a webpage ,insert malicious content into webpages , or alter the content of database.
- Compromised Availability of Data --- An attacker use this attack to delete the database information logs or audit information that is contained in database.
- Remote code Execution --- It allows an attacker to compromise the Host O.S.
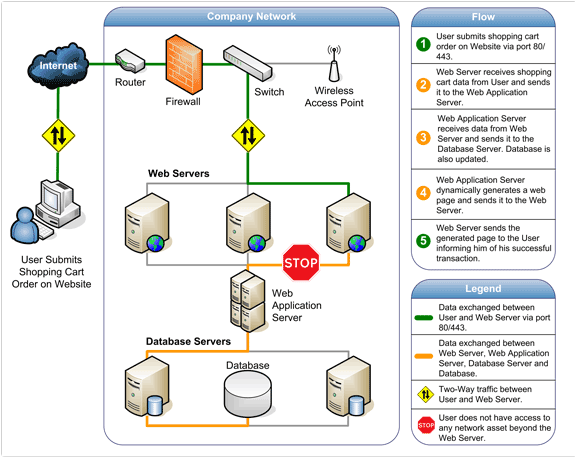
How web Application Works ----
- The above fig. shows how the initial request is triggered by the user through the browser over the Internet to the web application server.
- The web application accesses the databases servers to perform the requested task updating and retrieving the information lying within the database.
- The web application then presents the information to the user through the browser.
Web Security Issue ----
- web applications do raise a number of security concerns stemming from improper coding. Serious weaknesses or vulnerabilities, allow hackers to gain direct and public access to databases in order to sensitive data.
- Many of these databases contain valuable information (e.g., personal and financial details) making them a frequent target of hackers
- Websites and related web applications must be available 24 hours a day, 7 days a week, to provide the required service to customers, employees, suppliers and other stakeholders.
- Firewalls and SSL provide no protection against web application hacking, simply because access to the website has to be made public – All modern database systems (e.g. Microsoft SQL Server, Oracle and MySQL) may be accessed through specific ports (e.g., port 80 and 443) and anyone can attempt direct connections to the databases effectively bypassing the security mechanisms used by the operating system. These ports remain open to allow communication with legitimate traffic and therefore constitute a major vulnerability.
- Web applications often have direct access to back-end data such as customer databases and, hence, control valuable data and are much more difficult to secure. Those that do not have access will have some form of script that allows data capture and transmission. If a hacker becomes aware of weaknesses in such a script, he may easily reroute unwitting traffic to another location and illegitimately hive off personal details.
- Most web applications are custom-made and, therefore, involve a lesser degree of testing than off-the-shelf software. Consequently, custom applications are more susceptible to attack.
Types of SQL Injection ---
There are mainly TWO types of SQL injection ----
1. Simple SQL Injection
- Union SQL Injection
- Error Based SQL Injection.
2.Blind SQL Injection
okk....now the types of SQL injection related information I will post in My next blog...so GooD ByE frds....

No comments:
Post a Comment